AI is reshaping how work is done across enterprises. Less visibly, it is also reshaping how infrastructure behaves.
As organisations accelerate investments in AI platforms, data intensive workloads, and modern analytics, global demand for compute and memory has shifted toward large scale infrastructure. According to Gartner, By 2029, over 50% of enterprises will adopt AEM (Autonomous Endpoint Management) capabilities—up from nearly zero in 2024, signalling that AI driven endpoint and infrastructure decisions will soon become mainstream, not experimental.
This surge is being driven by hyperscaler and AI cluster demand for high bandwidth memory and DDR5, which is tightening DRAM supply and pushing prices up sharply in 2025–2026. IDC estimates that large enterprises will underestimate their AI infrastructure costs by around 30% through 2027, as GPU intensive workloads, inference cycles, and supporting systems consume far more capacity than traditional IT budgeting models anticipate. Against this backdrop, OEMs are already responding: reports indicate that laptop and desktop prices are set to rise by roughly 10–20% in early 2026 as memory driven bill of materials costs climb.
This shift is altering long established supply and pricing dynamics for core components such as RAM. The impact is now being felt well beyond data centres, most notably at the endpoint.
For enterprises with large user bases and hybrid operating models, laptops and desktops are becoming more expensive to procure, harder to standardise, and less predictable to refresh. What once appeared to be a procurement challenge is now intersecting with broader questions of scalability, security, and operational consistency. When external forces begin to influence how endpoint strategies are designed, secured, and sustained, the discussion moves beyond cost. It becomes architectural.
The Endpoint Is No Longer a Stable Foundation
Traditional endpoint models are built on a simple assumption: performance and security are delivered locally, on the device. Each user is issued hardware with sufficient compute and memory to meet their role’s requirements, supported by predictable refresh cycles.
That assumption is increasingly under strain.
Rising component costs and fluctuating availability introduce variability across the device estate. Standard configurations give way to mixed profiles. Refresh cycles stretch, not always by design, but by necessity. Over time, this variability creates friction across IT and security operations. Support overhead increases. Security baselines become harder to enforce consistently. Exceptions multiply, and governance becomes reactive rather than systematic.
In this environment, the endpoint shifts from being a reliable foundation to one of the least adaptable layers in the enterprise IT stack.
Moving the Control Plane Beyond the Device
A more resilient response is to reduce dependency on endpoint hardware rather than optimise around it.
Virtual desktop and application virtualisation change the centre of gravity for end user computing. Instead of embedding performance and memory capacity into every device, compute is centralised within controlled infrastructure and delivered securely to users. Endpoints function primarily as access layers, not execution environments.
This architectural shift has important implications. Performance scaling and capacity planning move into shared infrastructure, where variability can be managed more holistically. Endpoint lifecycles can be extended without compromising user experience, easing pressure on procurement and refresh planning. Standardised desktop environments simplify patching and updates, while enterprise data remains within centrally governed systems rather than being distributed across devices with varying risk profiles.
Whether adopted selectively or at scale, this model allows organisations to absorb hardware volatility rather than be driven by it.
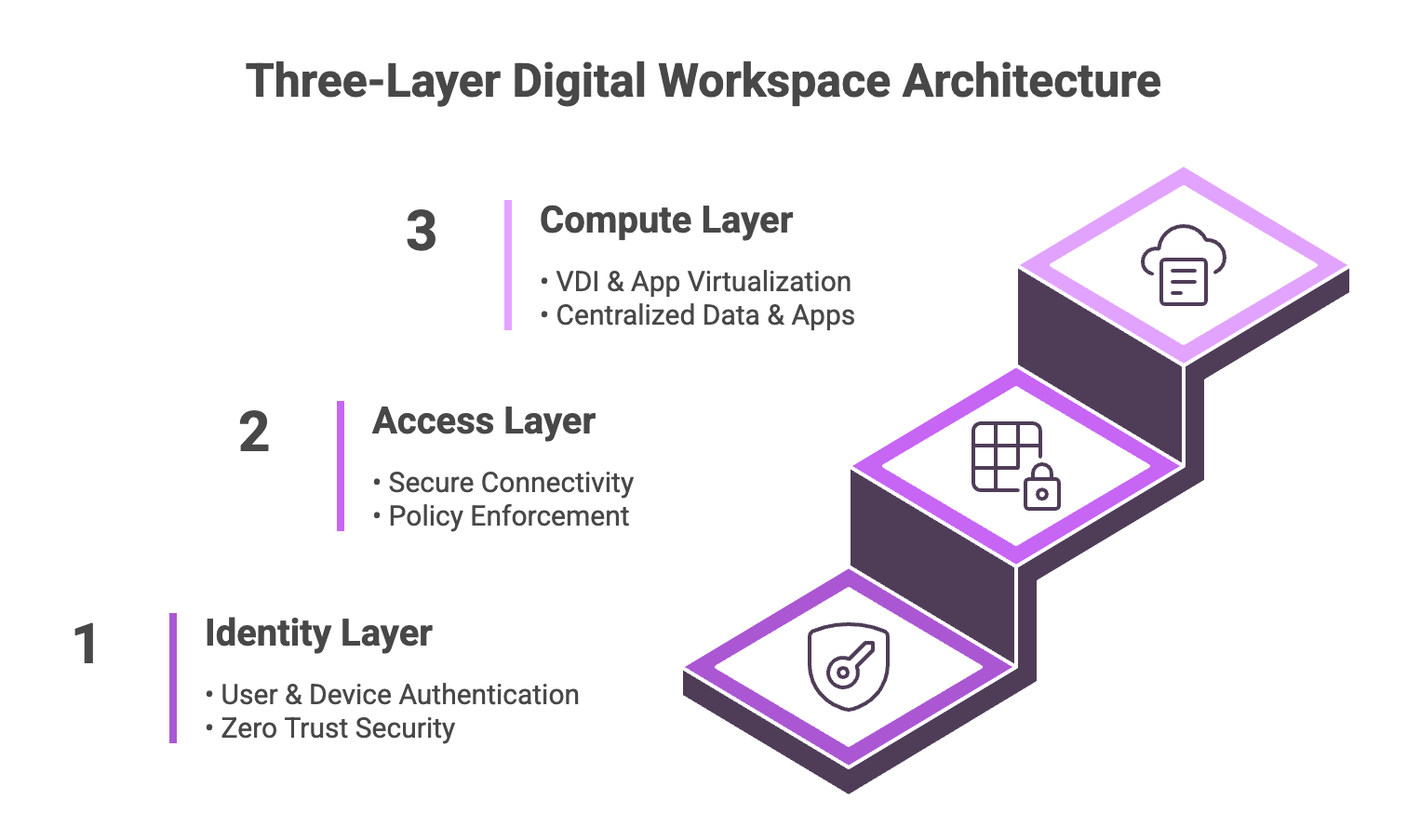
Security and Identity as the Anchor
Centralisation alone does not address the realities of modern enterprise access.
Users connect from multiple locations, networks, and devices, many of which sit outside traditional perimeter controls. In this context, secure delivery depends less on where a user connects from and more on who or what is requesting access.
Zero Trust principles ensure that every access request is evaluated continuously, based on identity and context. Session level controls, granular policy enforcement, and auditability become foundational requirements. When access is governed consistently, variation at the endpoint does not translate into variation in risk.
An integrated digital workspace approach, where virtualisation, secure access, and identity are designed together, ensures that simplifying endpoint hardware does not weaken governance. Instead, it strengthens it.
Accops brings these elements together within a unified digital workspace architecture, enabling organisations to centralise compute, enforce identity driven access, and maintain consistent control across users and locations without expanding the attack surface.
A Structural Response to a Structural Shift
Rising endpoint costs reflect a deeper shift in how infrastructure resources are prioritised globally. The question for organisations is not whether this volatility will persist, but how exposed their endpoint strategy is to it.
Architectures anchored to high specification devices will continue to absorb pricing swings and supply constraints. Models that decouple user experience from device economics, and anchor control at the workspace level, are inherently more resilient.
This is not about prescribing a single approach. It is about recognising that the economics of end user computing have changed, and that long term stability now depends on where performance, access, and security are designed to reside.
For CIOs, the first step is to identify high cost, high risk workloads—such as finance, engineering, and remote agent roles—and move them into a virtualised workspace environment where compute, data, and access controls are centralised. This reduces dependency on premium endpoints while improving security and standardisation.
Over the next three years, organisations can evolve from an endpoint heavy model to a workspace centric one by first focusing on pilots and consolidation, next expanding to broader user groups and standardising on a unified digital workspace platform, and finally tightening governance, automating patching and policy enforcement, and extending the model to hybrid and BYOD scenarios.

