In hospitals, access to clinical systems is often examined long after it occurs. A PACS image reviewed late at night, a laboratory report accessed remotely, or a patient record opened outside hospital premises can later become part of an audit, investigation, or medico-legal review.
As digital access expands to support on-call clinicians, remote diagnostics, and distributed care teams, hospitals are increasingly held accountable not just for who accessed clinical systems, but how, from where, and under what conditions that access took place. Enabling access is no longer sufficient. Access must be provable, traceable, and defensible.
This blog examines the security and compliance challenges that emerge when clinical access extends beyond traditional hospital boundaries, and why these challenges require architectural controls rather than isolated security tools.
Fragmented Governance Across Distributed Hospital IT Environments
Hospital IT environments are inherently decentralised across emergency departments, ICUs, operating theatres, diagnostic areas, ancillary services, and administrative functions. As hospital infrastructure grows, access to EMRs, PACS, laboratory systems, and clinical applications is often governed locally at workstations or departmental systems.
This decentralisation makes consistent governance difficult. Patching and remediation frequently require physical intervention in patient care areas, while visibility into who accessed which patient record, and when remains fragmented across systems.
From a compliance and audit perspective, this lack of centralised control introduces measurable risk. Hospital IT teams face significant challenges during:
- HIPAA audits requiring complete and consistent access logs
- Joint Commission reviews of system access controls
- Malpractice investigations that depend on precise access timelines
Solution: Centralised application and desktop delivery shifts execution into hospital-controlled infrastructure, enabling uniform policy enforcement, centralised audit trails, and ensuring PHI remains within controlled environments.
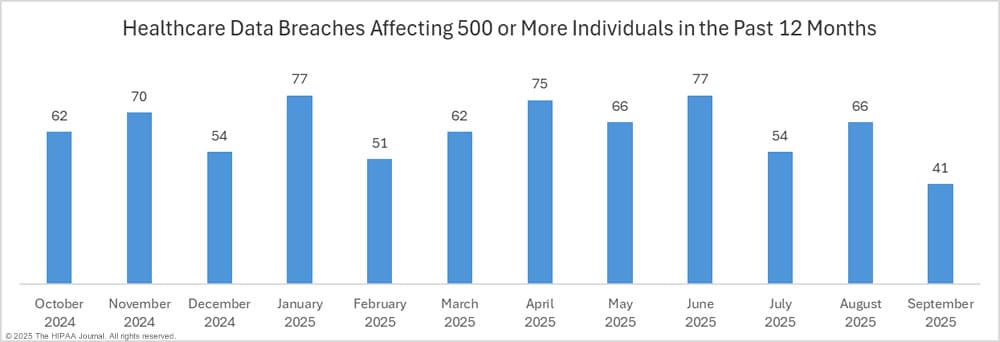
Source: Hipaajournal-September-2025-healthcare-data-breach-report
After-Hours Clinical Access as a Compliance Risk
After-hours access is a clinical necessity. Hospitalists, on-call specialists, and consulting physicians routinely access patient charts, diagnostic results, and lab reports to support emergency consults and inpatient decision-making.
In many hospitals, this access relies on VPNs or basic remote desktop tools. Clinicians connect from personal devices and home networks, achieving access but without consistent governance. IT teams often struggle to validate device posture, confirm clinical relevance, or maintain unified audit trails across systems.
Solution: A Zero Trust access model enforces session-level controls, validating identity, device health, and contextual parameters such as time and department before granting access. Sessions remain isolated, monitored, and centrally logged, preserving auditability without delaying care.
PHI Leakage and Loss of Data Control
As access extends beyond hospital-managed workstations, the primary risk shifts from unauthorised access to uncontrolled data handling. Even when authentication succeeds, hospitals often lack visibility into how PHI is handled within a session.
Sensitive data viewed through EMRs or PACS can be captured, printed, or transferred outside governed environments, complicating breach investigations and regulatory reporting. Hospitals must demonstrate not only authorised access, but also effective data protection controls.
Solution: Workspace-level controls restrict copy, paste, downloads, and local printing, apply watermarking, and enforce context-aware policies based on care setting. Centralised dashboards and audit logs provide real-time visibility and compliance-ready reporting.
Translating Architecture into Action
For hospital IT leaders, improving security and compliance starts with recognising where existing access models no longer align with operational and regulatory realities.
When access governance, PHI protection, and audit readiness are designed into the access architecture itself, hospitals move from reactive compliance to controlled, defensible operations, enabling digital care delivery to scale with confidence.

