Credential theft has witnessed a meteoric rise in the past couple of years with the surge in remote work. Reports suggest over 4/5th of data breaches resulting from hacking involve the use, or misuse, of lost or stolen credentials.
While the number may not be surprising, what is interesting though is that the attackers, in most cases, explore the same tried-and-tested approach: it starts with a phishing attack (mainly arrive by email) targeting a user’s endpoint and then crack weak passwords or steal credentials stored on the device. Once the attackers get their hands on these credentials, they can move from one workstation to another in search of sensitive data or privileged credentials (for example local admin rights) to gain access to higher-value assets and information.
With aggressive and destructive data breaches and credential thefts increasingly becoming commonplace, comprehending and preventing these threats is essential for any business. Not surprisingly, thus, a growing number of organizations are adopting an “identity-first” approach for managing security across the digital workspace.
Starting point: Define security based on criticality
Here is a basic framework for identifying what level of security should be imposed for accessing a given set of corporate applications.
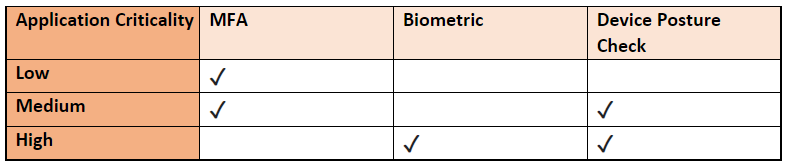
Organizations can classify their applications into three categories – low, medium, and high – based on their criticality, and accordingly, implement MFA, biometric authentication, and device posture check to minimize threat landscape.
Multi-factor authentication: Need of the hour
Passwords by themselves are not enough to secure the modern enterprise network from highly sophisticated cyberattacks. In fact, they are now recognized as a growing vulnerability, underlining the need for at least two forms of authentication to allow access to corporate applications and desktops.
Today, MFA is a basic security necessity. It provides an additional layer of security and ensures that only authenticated users can access corporate resources, preventing identity-related cyberattacks.
However, OTP, or push notification-based MFA, does not guarantee foolproof authentication. If a malicious user can gain access to the mobile device of an authenticated user and use the OTP or push notification, MFA’s purpose would be lost. Sophisticated cyberattacks are increasingly exploiting such drawbacks.
Biometric authentication: Stepping up security
Biometric authentication goes a step beyond conventional OTP-based or push notification-based MFA and provides foolproof authentication. Biometric authentication is based on ‘who the user is’, and not merely ‘what the user possesses’ like in case of OTP or push notification-based MFA. So, it is inherently much more secure than other forms of MFA.
But when it comes to mitigation of zero-day attacks, like malware, spyware, or ransomware attacks, any form of MFA can do little. Despite the presence of a biometric-based MFA mechanism, a malicious force can still exist undetected in the user device and can stealthily enter the corporate networks when an opportunity arises. In such a situation, device posture check should be imposed to grant or deny access.
Device posture check: Tackling zero-day attacks
Device posture check feature allows you to define security posture policies, and grants access only to those devices which follow these policies. The policies are typically defined in terms of device type, antivirus software status, security certificates, OS, OS versions, software patches, etc. After user authentication, the access gateway must scan the device for compliance and provides access only for compliant devices, while non-compliant devices are blocked from connecting to the internal network. Thus, device posture check provides an additional layer of security to corporate networks.
To conclude, organizations need to invest in technology and skills for modern identity and access management to ensure security across the hybrid workspace that is the new normal for businesses. IT teams must treat identity policy, process and monitoring as comprehensively as traditional LAN controls, with a special focus on remote workers and cloud computing.

