Dispersed workforce and diverse end-point devices connected over broadband and mobile networks have increased the corporate attack surface manifold, rendering business data and applications vulnerable like never before.
As such, firewalls, antivirus, access control and perimeter security monitoring are not enough to tackle ever-evolving malicious elements, which are lurking out there to exploit any kind of vulnerabilities in corporate networks or applications. What is needed is a different security framework that can help enterprises minimize the threat landscape, fend off increasingly elusive attackers and manage growing risks more efficiently.
Desktop virtualization provides an airgap security that enables organizations to deliver business applications and resources on demand; anywhere, anytime and via any network. It allows organizations to embrace work from anywhere and BYOD, without worrying about security risks, compliance issues or health of endpoint devices.
Increasing mobility & rising complexities
A large segment of the workforce is working from home today, accessing corporate applications and data from various locations, using varied devices and in different ways.
Business users, IT teams, support teams, developers, third party vendors and outsourced process users are accessing different kinds of applications — right from internal IT systems, helpdesk tools and end-user machines, UAT and production systems, to application servers, and customer VPNs.
As a result, critical business data no more resides within the corporate boundaries. It is everywhere: at employees’ homes located across geographies; corporate devices; personal laptops, tablets, or mobile phones; datacentres, private and public clouds, etc. Thus, data security and privacy are growing concerns for CIOs, CSOs and CTOs. To compound their worries, today’s cyber attackers have become more skilled and persistent in their malicious efforts, infecting enterprise resources through targeted hacking, malware and phishing attacks.
While tackling these new breeds of attackers is itself challenging enough, securing multiple types of endpoints spread across the geographies is a gigantic task. IT teams need to keep all applications and operating systems in each of those endpoint devices updated with the latest patches and hotfixes.
Measures aimed at preventing potential security breaches or cyberattacks are only a part of the tasks. IT should also ensure compliance with a series of national, international and industry-specific regulatory guidelines on data security and data privacy. Security requirements listed in contracts with partners and customers must be fulfilled to protect business interests of all the stakeholders.
Why traditional security architecture isn’t enough
Probably, the easiest way to tackle these complex challenges would be to ask all business users to work within the enterprise network, using only authorized corporate devices. No remote access or BYOD would be allowed.
But, a large number of users, even if not all, and their endpoints have long left the traditional corporate peripheries. Thus, the traditional security checks, which were effective within the corporate networks, aren’t enough to secure access by roaming or work-from-home users. As a result, IT, despite all the investments and efforts, is continuously failing to bridge the holes in the traditional security strategies and protect today’s complex computing environments.
This leads us to the question: how can enterprises regain control over data, applications and endpoints without hindering the business processes?
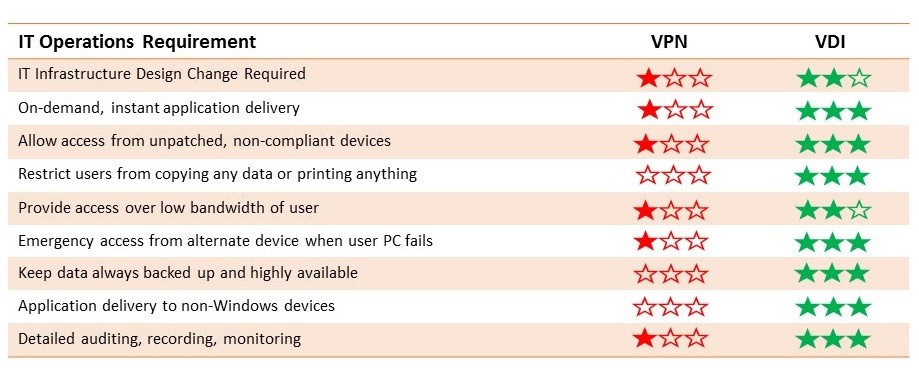
Generic VPN solutions fall short of meeting all the requirements, failing to bridge the gaps.
What IT can do is minimize the threat landscape through consolidation and centralization to meet data security, data protection, privacy and compliance requirement while maximizing business productivity and growth.
Security benefits of end user computing virtualization
- Centralization of Data & Management: The VDI moves all the computing and applications to the centralized datacentre, leaving no trace of data at the users’ endpoints. This helps consolidate all their applications and desktops management in a centralized location, while keeping governance with organizations. Organizations can control every device, applications & OS in their networks. Also, they can carry out software updates and fixes from one location, enhancing security and reducing IT operations costs.
- Protect Critical Applications by Isolation: Create an airgap between endpoints and business applications by running them in an isolated environment and hiding them from users’ devices and networks, preventing malware attacks and data leakage attempts.
- Safe Internet Browsing: Isolate internet from corporate networks via remote virtual browser, to keep the internal corporate networks clean and fend off possible cyberattacks.
- Avoid Network Bridging: Unlike generic L3/L4 VPN solutions, VDI doesn’t allow network bridging, thereby preventing malicious elements potentially residing in users’ endpoints from entering corporate network and infect busines resources.
- Secure Access for BYOD Users: Since all business applications are centralized, EUC virtualization helps IT to allow employees, consultants and vendors to use devices of their choice, without having to compromise with security or to hinder workflow.
- Contextual Access: Organizations can give access to business applications based on a user’s role and his or her access needs. No access is available to the users by default. And when the need arises, IT can revoke access rights in seconds.
- Device Entry Control: With EUC virtualization, enterprises can allow access to business application from only authorized or uncompromised devices. Therefore, there is no risk if a user brings a new device and tries to connect to the network. The user must go through corporate authentication to access business applications.
- Data Leakage Prevention: Users cannot copy-paste, download, print, screen-record or share screen while using virtual applications or virtual desktops. IT will have to make additional policy provision to allow above functions.
- Adhere to GDPR & Other regulations: EUC virtualization ensures that business is always in control of data, meeting existing data privacy guidelines as well as those coming up. Organizations can meet compliances related to enterprise computing by making the end user device non-significant and moving all management to the datacenter.
- Switch to Windows 10: Upgrade seamlessly to Windows 10 OS from the older versions to avail benefits of the latest features and security checks, without requiring changes in end devices.
- Data Backup & Recovery: With all the applications and data always residing in the datacentre, all the data generated by users are easily backed centrally. So even in case of any damage to the endpoint or theft of the device, the data is never lost.

